Modern security systems rely largely on technological innovations. And there's no denying that nowadays creation of reliable mechanisms of user data protection is one of the key concerns of security system developers.
One of the most popular methods to protect sensitive data and mission-critical systems involves using standalone, two factor authentication devices - USB devices or tokens - which provide hard disk encryption, email and transaction signing capabilities, and more.
Security tokens are used for identity and access management. The devices allow proving who you are while simultaneously protecting your sensitive information with advanced cryptography.
A typical hardware token is a small device designed in the form of a key fob. Some USB security tokens help store cryptographic keys such as electronic signature or biometric data (e.g., details of a fingerprint pattern). Some have a built-in protection against hacking, while others offer a mini-keyboard for entering a PIN code, or just a button (for starting the key generation procedure) and a display (for presenting the generated key). As a rule, USB security keys have a USB connector, support RFID functions, or use Bluetooth wireless interface to transfer the generated key sequence to the client system.
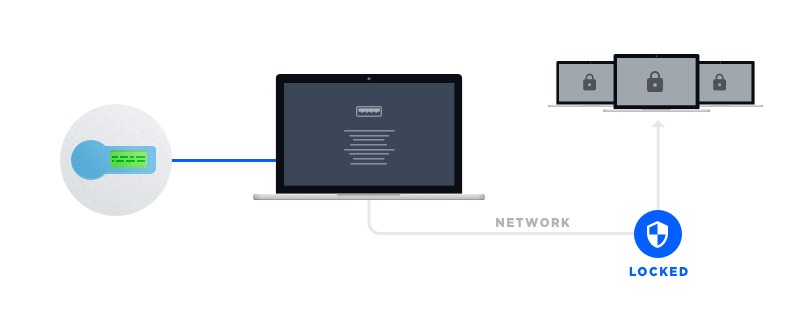
Current secure USB sticks act as an electronic key to access something. We connect to our personal accounts, the network of our company, or bank accounts from home, hotel, or cafe and do not even realize what damage this can cause to our personal or company data.
For instance, the customers who access their bank accounts over the network are out of the bank's physical control. Therefore, to enter some protected segments in the network from user workstations, it may be required to prove the identity of a person who is connecting to the account or corporate resources. All remote connections (including those done with the help of hardware tokens) can be processed by a dedicated software installed on a single data server. However, such software solution won't be able to control and process remote connections unless it supports a special technology of USB port virtualization that allows accessing USB tokens remotely.
In this regard, the developers of secure USB drives and software may face the virtualization challenge, as it will be required to not only build a dedicated USB redirection technology into hardware security tokens but also integrate the technology into a software system that will process remote token usage.
Electronic Team Port Virtualization Technology (EPVT) is the simplest and most efficient solution to this problem. EPVT is capable of redirecting any USB device over the network, making it available for remote access. With this solution, security system developers will get the ability to virtualize hardware tokens so that a control software can connect and manage them remotely. The technology can be easily integrated into both hardware tokens and dedicated processing software.
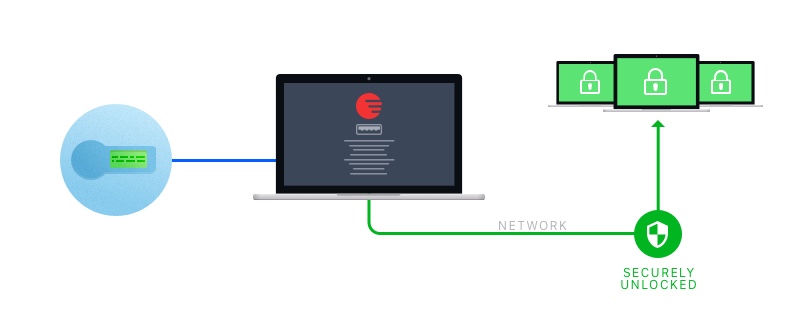
EPVT offers fully secure connections protected with advanced encryption and can be customized to fit the requirements of any specific security system.
SecureSystemIT